LDAP 基本概念
| 关键字 | 英文名称 | 介绍 |
|---|---|---|
| dc | Domain Compnent | 域名的部分,其格式是将完整的域名分成几部分,如域名为example.com变成dc=example,dc=com(一条记录的所属位置 |
| uid | User Id | 用户ID shuke.com(一条记录的ID) |
| ou | Organization Unit | 组织单位,组织单位可以包含其他各种对象(包括其他组织单元),如”oa组”(一条记录的所属组织) |
| cn | Common Name | 公共名称,如”Thomas Johansson”(一条记录的名称) |
| sn | Surname | 姓,如”赵” |
| dn | Distinguished Name | “uid=songtao.xu,ou=oa组,dc=example,dc=com”,一条记录的位置(唯一) |
| rdn | Relative dn | 相对辨别名,类似于文件系统中的相对路径,它是与目录树结构无关的部分,如”uid=tom”或”cn= Thomas Johansson” |
LDAP 部署文档
环境准备
1 | # cat /etc/issue |
一. 安装
- 安装软件包
1
2# apt install slapd ldap-utils -y
在安装过程中,将要求您输入并确认LDAP的管理员密码。 - 初始化配置
OpenLDAP 2.3 and later have transitioned to using a dynamic runtime configuration engine, slapd-config. Configuring slapd
1
2
3
4
5
6
7
8
9# dpkg-reconfigure slapd
1. Omit OpenLDAP server configuration: No
2. DNS domain name as base DN: shuke.net
3. Organization name: shuke Organization
4. Administrator password: shuke@2019
5. Database backend to use: MDB
6. Do you want the database to be removed when slapd is purged: No
7. Move old database: Yes
8. Allow LDAPv2 protocol? No - Configuration Layout
A sample config tree is shown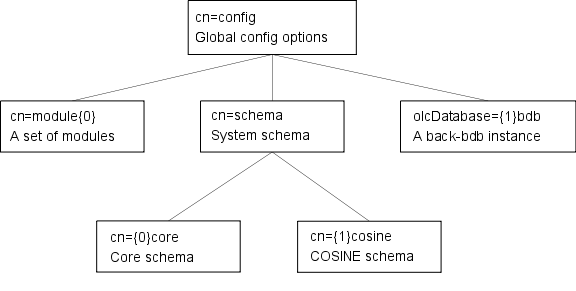
- 验证是否运行注: 软件默认安装路径为
1
2
3
4
5
6# ps -ef | grep slapd
openldap 11394 1 0 11:54 ? 00:00:00 /usr/sbin/slapd -h ldap:/// ldapi:/// -g openldap -u openldap -F /etc/ldap/slapd.d
root 11419 1227 0 11:55 pts/0 00:00:00 grep --color=auto slapd
# netstat -ntlp | grep 389
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 11394/slapd
tcp6 0 0 :::389 :::* LISTEN 11394/slapd/etc/ldap,mdb数据库文件存放路径为/var/lib/ldap/ - 测试LDAP的接口anonymous是匿名用户的查询结果,因为我们运行ldapwhoami而不登录到LDAP服务器.这意味着服务器正在运行并应答查询.
1
2# ldapwhoami -H ldap:// -x
anonymous - 启动停止至此,LDAP的初步基本配置已经完成.官方文档解释在2.3之后的版本使用动态的配置文件的方式,使用ldapadd, ldapdelete or ldapmodify修改更新配置信息以及数据库信息,不建议使用slapd.conf配置文件方式进行管理.
1
2# systemctl stop slapd.service
# systemctl start slapd.service
二. 查看初始化信息
1 | # ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=config dn |
三. TLS
- Install the gnutls-bin and ssl-cert packages
1
# apt install gnutls-bin ssl-cert
- Create a private key for the Certificate Authority
1
# sh -c "certtool --generate-privkey > /etc/ssl/private/cakey.pem"
- Create the template/file /etc/ssl/ca.info to define the CA
1
2
3cn = shuke Company
ca
cert_signing_key - Create the self-signed CA certificate
1
# certtool --generate-self-signed --load-privkey /etc/ssl/private/cakey.pem --template /etc/ssl/ca.info --outfile /etc/ssl/certs/cacert.pem
- Make a private key for the server
1
# certtool --generate-privkey --sec-param Medium --outfile /etc/ssl/private/tldap.shuke.net-key.pem
- Create the /etc/ssl/tldap.shuke.net.info info file containing
1
2
3
4
5
6organization = shuke Company
cn = tldap.shuke.net
tls_www_server
encryption_key
signing_key
expiration_days = 3650 - Create the server’s certificate
1
# certtool --generate-certificate --load-privkey /etc/ssl/private/tldap.shuke.net-key.pem --load-ca-certificate /etc/ssl/certs/cacert.pem --load-ca-privkey /etc/ssl/private/cakey.pem --template /etc/ssl/tldap.shuke.net.info --outfile /etc/ssl/certs/tldap.shuke.net.pem
- Adjust permissions and ownership
1
2
3
4
5
6
7# mkdir /etc/ldap/certs
# cp /etc/ssl/private/tldap.shuke.net-key.pem /etc/ldap/certs/
# cp /etc/ssl/certs/cacert.pem /etc/ldap/certs/
# cp /etc/ssl/certs/tldap.shuke.net.pem /etc/ldap/certs/
# chown -R openldap.openldap /etc/ldap/certs/
# chmod 0640 /etc/ssl/private/tldap.shuke.net-key.pem
# gpasswd -a openldap ssl-cert - Create the file certinfo.ldif
1
2
3
4
5
6
7
8
9
10
11
12# cat certinfo.ldif
# create new
dn: cn=config
changetype: modify
add: olcTLSCACertificateFile
olcTLSCACertificateFile: /etc/ldap/certs/cacert.pem
-
replace: olcTLSCertificateFile
olcTLSCertificateFile: /etc/ldap/certs/tldap.shuke.net.pem
-
replace: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/ldap/certs/tldap.shuke.net-key.pem - Use the ldapmodify command to tell slapd about our TLS work via the slapd-config database
1
2
3
4
5# ldapmodify -Y EXTERNAL -H ldapi:/// -f certinfo.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "cn=config" - Contratry to popular belief, you do need Add
ldaps:///in /etc/default/slapd in order to use encryption. You should have just1
2# vim /etc/default/slapd
SLAPD_SERVICES="ldap:/// ldapi:/// ldaps:///" - 修改请求域名
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41# cat slapd.ldif
# log
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
-
add: olcIdleTimeout
olcIdleTimeout: 30
-
add: olcReferral
olcReferral: ldaps://tldap.shuke.net
-
add: olcLogFile
olcLogFile: /var/log/sladp.log
# ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f slapd.ldif
modifying entry "cn=config"
# ldapsearch -Y external -H ldapi:/// -b cn=config "(objectClass=olcGlobal)" olcReferral
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
# extended LDIF
#
# LDAPv3
# base <cn=config> with scope subtree
# filter: (objectClass=olcGlobal)
# requesting: olcReferral
#
# config
dn: cn=config
olcReferral: ldaps://tldap.shuke.net
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1 - restart slapd
1
2
3
4
5
6# systemctl restart slapd.service
# netstat -ntlp | grep slapd
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 13728/slapd
tcp 0 0 0.0.0.0:636 0.0.0.0:* LISTEN 13728/slapd
tcp6 0 0 :::389 :::* LISTEN 13728/slapd
tcp6 0 0 :::636 :::* LISTEN 13728/slapd
四. 验证数据
- 初始化一些数据此时,使用客户端工具phpLDAPadmin或者LDAP Admin Tool访问LDAP server端即可以查看到数据.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35# cat add_content.ldif
dn: ou=People,dc=example,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Groups,dc=example,dc=com
objectClass: organizationalUnit
ou: Groups
dn: cn=miners,ou=Groups,dc=example,dc=com
objectClass: posixGroup
cn: miners
gidNumber: 5000
dn: uid=john,ou=People,dc=example,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: john
sn: Doe
givenName: John
cn: John Doe
displayName: John Doe
uidNumber: 10000
gidNumber: 5000
userPassword: johnldap
gecos: John Doe
loginShell: /bin/bash
homeDirectory: /home/john
# ldapadd -x -W -D "cn=admin,dc=shuke,dc=net" -f add_content.ldif
Enter LDAP Password: ********
adding new entry "ou=People,dc=example,dc=com"
adding new entry "ou=Groups,dc=example,dc=com"
adding new entry "cn=miners,ou=Groups,dc=example,dc=com"
adding new entry "uid=john,ou=People,dc=example,dc=com" - 查询目录结构树
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26# ldapsearch -x -LLL -H ldap:/// -b dc=shuke,dc=net dn
dn: dc=shuke,dc=net
dn: cn=admin,dc=shuke,dc=net
dn: ou=Hosts,dc=shuke,dc=net
dn: ou=Devops,dc=shuke,dc=net
dn: ou=Groups,dc=shuke,dc=net
dn: ou=People,dc=shuke,dc=net
dn: ou=Marketing,dc=shuke,dc=net
dn: ou=department,dc=shuke,dc=net
dn: cn=iris+ipHostNumber=192.168.1.51,ou=Hosts,dc=shuke,dc=net
dn: cn=gojira+ipHostNumber=192.168.1.1,ou=Hosts,dc=shuke,dc=net
dn: cn=zedan+ipHostNumber=192.168.1.52,ou=Hosts,dc=shuke,dc=net
dn: cn=gamera+ipHostNumber=192.168.1.50,ou=Hosts,dc=shuke,dc=net
dn: cn=git-shuke01cn-p001.pek3.shuke.net,ou=Hosts,dc=shuke,dc=net
dn: uid=shuke,ou=Devops,dc=shuke,dc=net
dn: cn=dba,ou=Groups,dc=shuke,dc=net
dn: cn=devops,ou=Groups,dc=shuke,dc=net
dn: cn=tester,ou=Groups,dc=shuke,dc=net
dn: cn=manager,ou=Groups,dc=shuke,dc=net
dn: cn=developer,ou=Groups,dc=shuke,dc=net
dn: cn=Pete Minsky,ou=Marketing,dc=shuke,dc=net
# 账号登录认证
# ldapwhoami -H ldapi:/// -x -D cn=admin,dc=shuke,dc=net -W
Enter LDAP Password:
dn:cn=admin,dc=shuke,dc=net
五. Logging设置
- Create the file logging.ldif with the following contents
1
2
3
4
5# cat logging.ldif
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats - 更新数据
1
# ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f logging.ldif
- 在/etc/rsyslog.conf增加内容
1
2
3# Disable rate limiting
# (default is 200 messages in 5 seconds; below we make the 5 become 0)
$SystemLogRateLimitInterval 0 - restart the rsyslog daemon此时,
1
systemctl restart syslog.service
tail -f /var/log/syslog查看日志文件内容,可以查看到LDAP相关log
六. LDAP命令介绍
1 | ldapmodrdn 命令用于对 OpenLDAP 目录树中 RDN 条目的修改,可以从标准的条目信息输入或者使用 -f 指定 LDIF 文件的格式输入。 |
dn: uid=shuke,ou=stuff,dc=shuke,dc=com
givenName: shu
sn: ke
userPassword:: e01ENX00UXJjT1VtNldhdStWdUJYOGcrSVBnPT0=
gidNumber: 5000
homeDirectory: /home/shuke
loginShell: /bin/bash
cn: shuke
uid: shuke
uidNumber: 1100
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
objectClass: person
objectClass: ldapPublicKey
sshPublicKey: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDRMPwi6Q/Zcb1N6sWnFf5/EwTv
mpfEZyRI0XUnCtZKWEPPCbgjPfQ2ZKYPCsmfvqA6uaVolBzLM04BZEbbeHmC1mB3kpvOXmZtH7iAt
22khCyS5A/jzaE9lwgyGzO/mhJQ83EIBt4MtO/UgGyk1EAyQH0gAGgfqQ2Htyp44wxul0plpbcmTE
lQQUZiLMNUspKS4i3BDGSWwu+Y2q7h3jTfgMpyLweqnt4vuUwhaGouP1P6q7M7HCRMKbXL5MH3K0s
z5G1WpiqsXxtHbFgQZiniOwO/EaUvca9MQRwY5zeMxkUJ38HlpvRjp16HevpuLqvUqy2Uw2migJNW
52ZubtGlOzc8mJh/qSLUTV1238Z6dgR6nELa260RnsPNp3Utb7HkhY6WZSRYxNxjvsGWDIKMczPHb
fhHf0iuuxGt96dPhpM6V8UH0zbPUEL/6+VRTMThflewLA+2/9J5VzG+Ugqm3vU3jVZxgMqqFlJmI9
nfw0/H+1H+6AEU556fNTqBFQAEQDNKltv4hv/YLmpcYh7lSJU9TjHaHCXpbLDaAQPLcNBFzA1lL3K
U+rx1xwww4Tbn77qU/JmSACLP/oczrLvb+kLjO2dyi0WfEjqgeIn83OPPv4CtTMlpHZj2kP2L7Sw8
RZHXurL1wLqBnVrCGzHcC2huB9jn3QUedWjVqdA6Sw== shuke@shukes-mbp
[root@tldap ldap]# ldapsearch -x -LLL cn=sre
dn: cn=sre,ou=groups,dc=shuke,dc=com
cn: sre
objectClass: posixGroup
objectClass: top
gidNumber: 5000
description: sre group
memberUid: uid=wangwu,ou=stuff,dc=shuke,dc=com
memberUid: uid=guoliman,ou=stuff,dc=shuke,dc=com
memberUid: uid=fengfengzhao,ou=stuff,dc=shuke,dc=com
memberUid: uid=shuke,ou=stuff,dc=shuke,dc=com
memberUid: uid=mazengsui,ou=stuff,dc=shuke,dc=com
1 | LDAP客户端机器验证: |
七. 卸载LDAP
- 命令卸载
1
# apt-get purge --auto-remove slapd ldap-utils
- 删除目录
1
# rm -rf /etc/ldap && rm -rf /var/lib/ldap
八. Backup and Restore
- 下载脚本文件
1
2
3
4wget --no-check-certificate https://raw.githubusercontent.com/alexanderjackson/ldap-backup-and-restore/master/ldap-backup -O /usr/local/sbin/ldap-backup
wget --no-check-certificate https://raw.githubusercontent.com/alexanderjackson/ldap-backup-and-restore/master/ldap-restore -O /usr/local/sbin/ldap-restore
chown root.root /usr/local/sbin/ldap-backup /usr/local/sbin/ldap-restore
chmod 500 /usr/local/sbin/ldap-backup /usr/local/sbin/ldap-restore - 备份脚本
1
2
3
4
5
6
7
8
9
10
11
12
13# grep -v '^#' /usr/local/sbin/ldap-backup
TIMESTAMP=$(date +%Y%m%d-%H%M%S)
BACKUP_PATH=/data/backups/ldap/${TIMESTAMP}
echo " Creating backup at ${BACKUP_PATH}"
mkdir -p ${BACKUP_PATH}
/usr/bin/nice /usr/sbin/slapcat -n 0 > ${BACKUP_PATH}/config.ldif
/usr/bin/nice /usr/sbin/slapcat -n 1 > ${BACKUP_PATH}/domain.ldif
/usr/bin/nice /usr/sbin/slapcat -n 2 > ${BACKUP_PATH}/access.ldif
chmod 640 ${BACKUP_PATH}/*.ldif
tar cpzf ${BACKUP_PATH}/etc_ldap.tgz /etc/ldap >/dev/null 2>&1
tar cpzf ${BACKUP_PATH}/var_lib_ldap.tgz /var/lib/ldap >/dev/null 2>&1
ls -ahl ${BACKUP_PATH}
echo "Run ldap-restore to restore previous backups..." - 计划任务
1
2
3# cat /etc/cron.d/ldap-backup
MAILTO=yunwei@shuke.net
0 0 * * * root /usr/local/sbin/ldap-backup - 恢复LDAP数据参考脚本文件:
1
2
3
4
5
6
7
8sudo systemctl stop slapd.service
sudo mkdir /var/lib/ldap/accesslog
sudo slapadd -F /etc/ldap/slapd.d -n 0 -l /data/backups/ldap/${TIMESTAMP}/config.ldif
sudo slapadd -F /etc/ldap/slapd.d -n 1 -l /data/backups/ldap/${TIMESTAMP}/domain.com.ldif
sudo slapadd -F /etc/ldap/slapd.d -n 2 -l /data/backups/ldap/${TIMESTAMP}/access.ldif
sudo chown -R openldap:openldap /etc/ldap/slapd.d/
sudo chown -R openldap:openldap /var/lib/ldap/
sudo systemctl start slapd.service
GitHub - alexanderjackson/ldap-backup-and-restore
How To Backup and Restore OpenLDAP - Tyler’s Guides
ldap3 client example
ldapPublicKey
- 配置文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17# cat openssh-lpk.ldif
# LDAP SSH Public Key schema
# Source: https://serverfault.com/questions/653792/ssh-key-authentication-using-ldap
# Homepage: https://github.com/AndriiGrytsenko/openssh-ldap-publickey
dn: cn=openssh-lpk,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: openssh-lpk
olcAttributeTypes: ( 1.3.6.1.4.1.24552.500.1.1.1.13 NAME 'sshPublicKey'
DESC 'MANDATORY: OpenSSH Public key'
EQUALITY octetStringMatch
SYNTAX 1.3.6.1.4.1.1466.115.121.1.40 )
olcObjectClasses: ( 1.3.6.1.4.1.24552.500.1.1.2.0 NAME 'ldapPublicKey'
DESC 'MANDATORY: OpenSSH LPK objectclass'
SUP top AUXILIARY
MAY ( sshPublicKey $ uid )
) - 导入配置信息此时,可以使用sshPublicKey属性进行user登录验证.
1
2
3
4
5# ldapadd -Y EXTERNAL -H ldapi:/// -f openssh-lpk.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=openssh-lpk,cn=schema,cn=config"
LDAP server端配置sudo
1 | # cat exports.ldif |
OpenLDAP Sudo 权限讲解
OpenLDAP Sudo 规则
Q&A
- 如何修改默认的数据库文件创建路径?
默认的数据库文件路径是/var/lib/ldap
创建存放DB数据的路径,并修改权限
1
2# mkdir /data/ldap/data -pv
# chown -R openldap.openldap /data/ldap/data编写修改db路径的ldif文件
1
2
3
4
5# cat dbpath.ldif
dn: olcDatabase={1}mdb,cn=config
changetype: modify
replace: olcDbDirectory
olcDbDirectory: /data/ldap/data执行修改命令,提示错误信息如下
1
2
3
4ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f dbpath.ldif
adding new entry "olcDatabase={1}hdb,cn=config"
ldap_add: Other (e.g., implementation specific) error (80)
additional info: olcDbDirectory: value #0: invalid path: Permission deniedlog信息
ldap启动失败,/var/log/syslog日志显示:olcDbDirectory: value #0: invalid path: Permission denied问题原因
AppArmor的配置导致AppArmor (Application Armor) 是一个类似于 SELinux 的一个强制访问控制方法,通过它你可以指定程序可以读、写或运行哪些文件,是否可以打开网络端口等。AppArmor 配置比 SELinux 更加方便比较适合学习
I believe if you want to install the LDAP Db to another directory you would need to add that directory to the apparmor profile for slapd. In my case that would have been editing “/etc/apparmor.d/usr.sbin.slapd” and changing解决方法
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16# vim /etc/apparmor.d/usr.sbin.slapd
# the databases and logs
/var/lib/ldap/ r,
/var/lib/ldap/** rwk,
# lock file
/var/lib/ldap/alock kw,
/data/ldap/data/ r,
/data/ldap/data/** rwk,
# lock file
/data/ldap/data/alock kw,
添加DB路径到配置文件中,如上所示
重启apparmor服务
# /etc/init.d/apparmor restart修改路径
1
2
3
4# ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f dbpath.ldif
modifying entry "olcDatabase={1}mdb,cn=config"
重启ldap服务
# systemctl restart slapd.service查看验证
1
2
3
4
5
6# ldapsearch -H ldapi:// -Y EXTERNAL -b "olcDatabase={1}mdb,cn=config" "(objectClass=olcDatabaseConfig)" olcDbDirectory -LLL
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
dn: olcDatabase={1}mdb,cn=config
olcDbDirectory: /data/ldap/data
- 如何设置LDAP管理员密码?
- 生成密码
1
2
3
4# slappasswd
New password:
Re-enter new password:
{SSHA}XsxctHt+Ae3Saq2Kcead4UdZ0kOTZRn8 - 生成LDIF文件
1
2
3
4
5
6cat << EOF > chrootpw.ldif
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}XsxctHt+Ae3Saq2Kcead4UdZ0kOTZRn8
EOF - 执行LDIF文件
1
# ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif
refs
主要参考资料
OpenLDAP Server
OpenLDAP - OpenLDAP - Wiki.Shileizcc.com
OpenLDAP Software 2.4 Administrator’s Guide: Configuring slapd
其他参考
我花了一个五一终于搞懂了OpenLDAP - 日新亭 - SegmentFault 思否
Enable the production of Openldap Log file - Tutoriels pour la construction de logiciels
OpenLDAP 初识 | Mallux - 宁静致远
OpenLDAP — Linux Guide and Hints
Ubuntu 17.04 : Create SSL Certificates : Server World
OpenLDAP Server
如何使用LDIF文件来进行更改OpenLDAP系统
LDAP Admin Tool
ldap over ssl